Bot Management and DDoS Mitigation
Bot Management provides advanced automated traffic detection and mitigation capabilities using machine learning algorithms to classify, challenge, and control bot traffic while ensuring legitimate users have uninterrupted access.
Current Service Status
Important: Bot Management uses real-time ML models updated every 30 minutes for optimal detection accuracy and minimal false positives
Quick Start
For Basic Bot Protection Setup
- Enable Search Engine Allowlist - Allow legitimate crawlers (Google, Bing) to bypass challenges
- Block Security Scanners - Automatically block vulnerability scanners and security tools
- Configure Challenge Methods - Set up CAPTCHA or JavaScript challenges for suspicious traffic
- Monitor Bot Activity - Review bot classification reports and adjust settings
Bot Management
Application Layer
The Application Layer configuration in Bot Management provides application-layer DDoS protection (Layer 7) measures to prevent access from automated tools or malicious bots. The options in this section are designed based on bot classification lists researched, compiled, and evaluated by the VNIS technical team. Each option can be enabled/disabled with toggle switches, and users can click the eye icon to view detailed lists applied for each type.
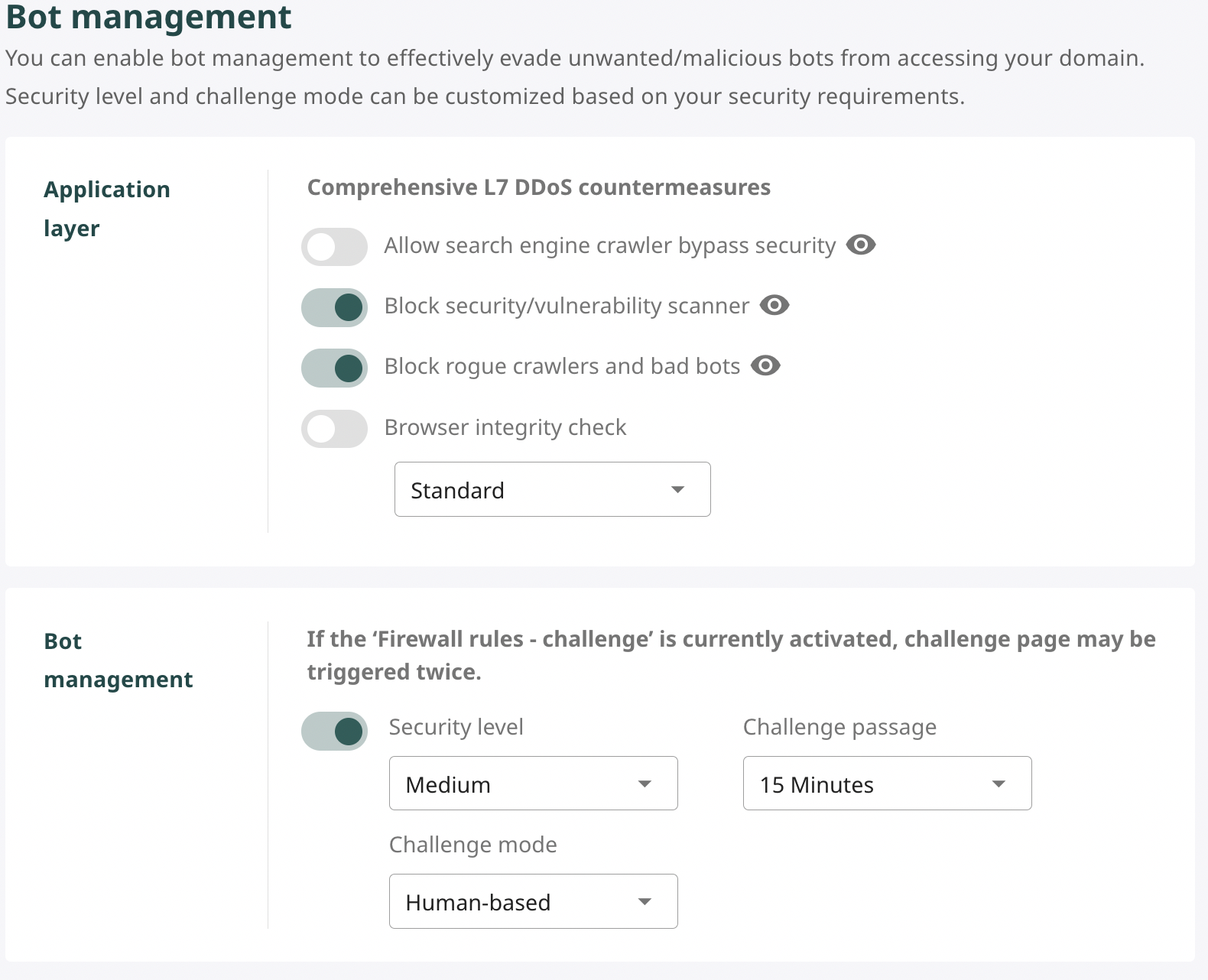
Configuration options include:
-
Allow search engine crawler bypass security Allows trusted search engine crawlers (such as Googlebot, Bingbot) to bypass bot checking layers. If disabled, all crawlers will be treated as regular bots.
-
Block security/vulnerability scanner Blocks vulnerability scanning and security testing tools (e.g., Acunetix, Nessus, Nikto...) commonly used by attackers to probe system weaknesses.
-
Block rogue crawlers and bad bots Blocks invalid crawlers, automated bots causing heavy load, spam, or unauthorized information collection from the system.
These bot groups are regularly updated by VNIS based on behavior lists and fingerprints collected from real systems.
Browser Integrity Check
The Browser Integrity Check feature helps validate browser access based on HTTP headers, especially the User-Agent field. The system will automatically apply challenges if it detects access without or using abnormal User-Agent (e.g., empty, spoofed, or from bot tools).
-
When this feature is enabled, invalid access will be blocked or put through verification processes.
-
Checking levels can be configured:
- Standard (default): Basic blocking based on clear abnormal signs.
- Strict: More stringent checking, including blocking crawlers from unclear sources or suspected spoofing.
This feature is particularly useful for detecting spontaneous bots or custom crawler tools.
Bot Management Configuration
In addition to application-layer bot prevention measures, the system provides challenge configuration to handle suspicious traffic through multi-layer authentication mechanisms. Users can fine-tune security levels and intelligent response mechanisms to minimize malicious bots while ensuring legitimate access experience.
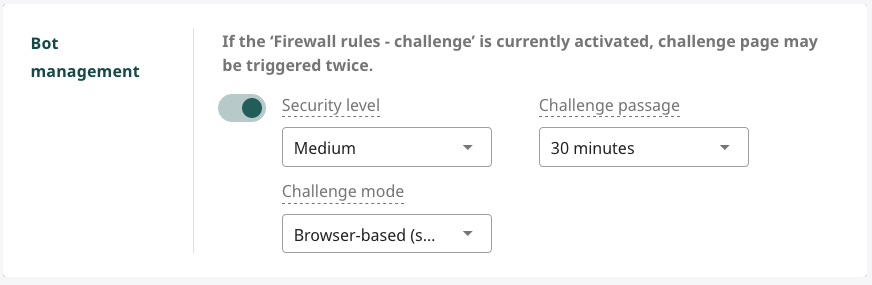
The configuration includes three main components:
Security Level
Allows adjusting system sensitivity to activate challenge mechanisms. The system monitors the number of requests per minute from the same access address and compares it with request threshold or token request threshold:
- If thresholds are exceeded, the system will require authentication challenges.
- If an authenticated token continues to send too many requests exceeding token limits, challenges will be reactivated.
Threshold table for each security level:
| Security Level | Request Threshold | Token Request Threshold |
|---|---|---|
| Under attack | 0 | 0 |
| High | 0 | 10 |
| Medium | 1000 | 60 |
| Low | 2000 | 60 |
| Essentially off | 3000 | 60 |
Challenge Passage Time
Sets the validity time for passed challenge results. During this period, users will not be challenged again. After the time expires, the system will reevaluate subsequent access and may require verification again if thresholds continue to be exceeded.
Example: If set to 30 minutes, users after passing the challenge will be exempt from verification for the next 30 minutes.
Challenge Mode
Challenge mode options suitable for different access situations:
- Browser-based (no delay): Simple JavaScript check with no waiting time — suitable for detecting simple bots without affecting user experience.
- Browser-based (standard): JavaScript check with 5-second countdown before processing requests.
- Human-based: Apply CAPTCHA verification "I am not a robot" before allowing continuation — suitable for situations requiring strict checking.
This configuration should be adjusted based on risk level, service type, and content sensitivity on the system. For public systems, it's recommended to choose light modes like Browser-based (standard) combined with Medium security level to balance security and experience.
Getting Support
Bot Detection Configuration: Access VNIS security experts for bot management setup and ML model optimization
False Positive Analysis: Get specialized support for reducing false positives while maintaining security effectiveness
Advanced Challenge Setup: Expert guidance for custom challenge configurations and user experience optimization
Performance Monitoring: 24/7 monitoring and support for bot management performance and effectiveness